
Mastering Real-Time Language Translation for Seamless Multiplayer Gaming: Top Strategies for Fluent Communication
Overview of Language Barriers in Multiplayer Gaming Language barriers present significant challenges in multiplayer gaming, often impeding seamless player experiences and effective teamwork. As gaming[…]

Endless Urban Realms: The Impact of Procedural Generation on the Future of City-Building Games
Understanding Procedural Generation Procedural Generation in gaming is a fascinating process that uses algorithms to create content dynamically, rather than relying on manually designed assets.[…]

Crucial strategies for building a strong email gateway to combat phishing threats
Understanding Phishing Threats Phishing represents a significant risk in the digital landscape, affecting both individuals and organizations. A comprehensive understanding of phishing threats reveals their[…]

Unlocking the Roadblocks: Challenges of Voice-Controlled Interfaces in Strategy Games Revealed
Unlocking the Roadblocks: Challenges of Voice-Controlled Interfaces in Strategy Games Revealed to Voice-Controlled Interfaces in Gaming Voice-controlled interfaces have revolutionized the way we interact with[…]
Essential guide to configuring kong api gateway for secure microservices architecture: a comprehensive walkthrough
Overview of Kong API Gateway The Kong API Gateway is a highly versatile platform designed to manage, secure, and route API traffic efficiently within a[…]
Comprehensive blueprint for establishing secure ssh access via public key authentication on your linux server
Understanding SSH and Public Key Authentication SSH (Secure Shell) is a protocol designed to provide secure access to remote servers. This robust security mechanism is[…]

Essential tactics for protecting kubernetes clusters in a multi-tenant environment
Access Control Strategies In the realm of Kubernetes security, effectively managing access control is paramount. One pivotal strategy involves implementing Role-Based Access Control (RBAC). This[…]

Essential tips for building a secure and efficient home automation system using your google nest hub
Setting Up Your Google Nest Hub for Home Automation Setting up your Google Nest Hub is an essential step toward transforming your home into a[…]
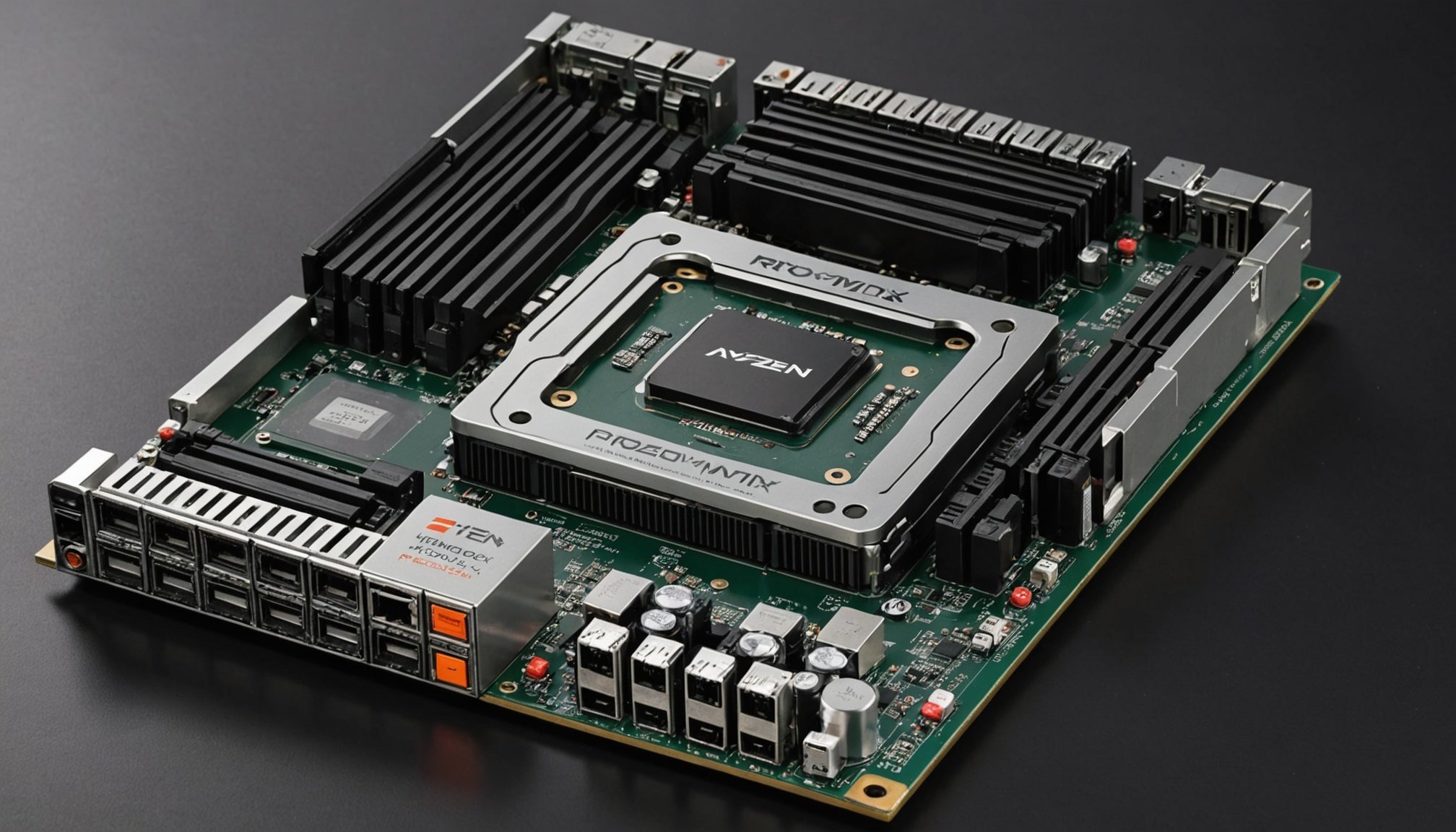
Unlocking the power of proxmox ve: a comprehensive guide to building a high-performance virtualization server on your amd ryzen 9 5900x
Unlocking the Power of Proxmox VE: A Comprehensive Guide to Building a High-Performance Virtualization Server on Your AMD Ryzen 9 5900X Why Choose Proxmox VE[…]

Essential elements for developing innovative ai-driven wearable tech apps
Critical Components of AI-Driven Wearable Tech Apps Artificial intelligence integration in wearable technology is reshaping user interactions and functionalities. A solid understanding of the critical[…]









