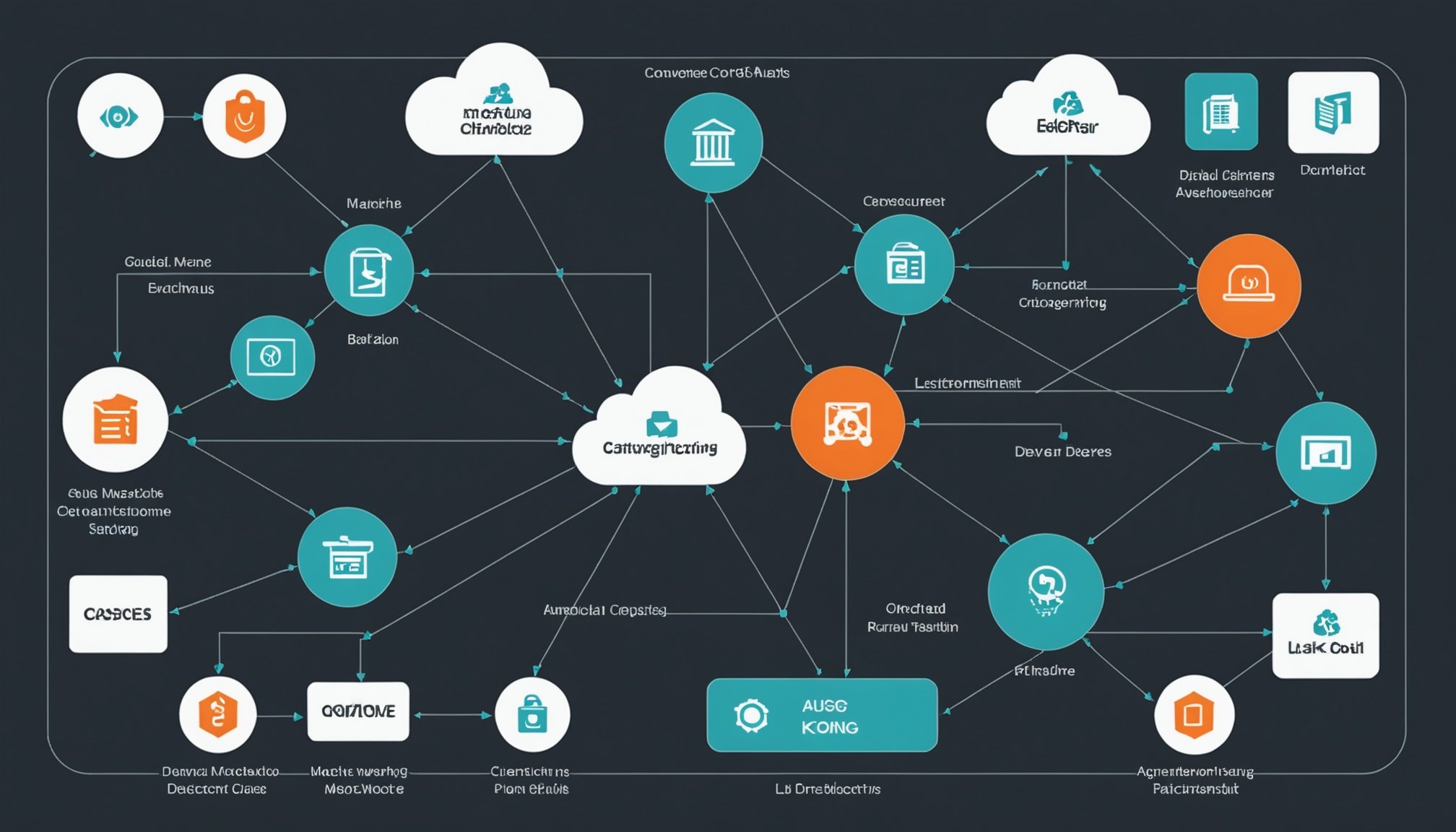
Overview of Kong API Gateway
The Kong API Gateway is a highly versatile platform designed to manage, secure, and route API traffic efficiently within a microservices architecture. It acts as an intermediary between clients and services, simplifying the complexity of interactions. In a microservices architecture, where services are often distributed and independent, Kong ensures seamless communication and management, thereby enhancing system reliability and performance.
Security features are paramount in the Kong API Gateway, providing robust measures to protect data and services. It offers crucial components such as authentication, rate limiting, and OAuth integration to shield APIs from malicious attacks and unauthorized access. These security features ensure that sensitive data remains secure, maintaining the integrity and privacy of user information.
Also to see : Comprehensive blueprint for establishing secure ssh access via public key authentication on your linux server
Kong’s ability to dynamically scale in response to traffic demands makes it an indispensable tool for businesses aiming to adopt a microservices architecture. Its security measures not only safeguard against threats but also foster a trustworthy environment for digital transactions. For organizations, this translates into a resilient API management system that boosts service performance while ensuring comprehensive security. By integrating security features and enhancing API management, Kong API Gateway stands out as a formidable solution for modern digital infrastructures.
Installation Process
Installing Kong requires an understanding of specific system requirements and setup instructions. Prior to proceeding with installation, ensure that your system meets the prerequisites. These typically include a Linux-based operating system for optimal compatibility; however, Kong can also be configured on macOS and Windows environments through various containerized options like Docker. Required software components often involve a dependency on a database, such as PostgreSQL or Cassandra, to manage Kong’s configuration data.
This might interest you : Mastering the art of unsend: a guide for gmail users
Setup Instructions
-
Initial Setup: Begin by installing necessary dependencies and confirming your system’s preparedness for Kong’s installation. This usually involves package management via tools like
aptoryumdepending on your operating system distribution. -
Database Configuration: Choose and set up a compatible database. Both PostgreSQL and Cassandra are robust choices. Ensure your database server is properly configured to handle Kong’s demands by adjusting settings for performance and resilience.
-
Kong Installation: Utilize installation commands specific to your operating system. For instance, on Ubuntu, you might use
sudo apt-get install kong.
Common Installation Issues and Troubleshooting
If you encounter difficulties, common issues often stem from unresolved dependencies or incorrect database configurations. Ensure all prerequisites are adequately addressed and consult Kong’s comprehensive documentation for specialised troubleshooting techniques.
Initial Configuration
Setting up your Kong environment requires attention to basic settings within a configuration file. The file, often named kong.conf, defines operational parameters. It is crucial to tailor this configuration to match your setup needs, adjusting fields such as log_level for debugging or proxy_listen to define network interfaces.
Configuration File
The configuration file serves as the blueprint for Kong’s initial behaviour. This file should be edited to reflect your system’s needs, such as specifying the database option to choose between PostgreSQL and Cassandra. Modifying admin_listen allows you to set which IP address the administrative interface will run on, a key step in ensuring accessibility only to trusted networks.
Setting Up Databases
Kong supports PostgreSQL and Cassandra. For PostgreSQL, establish a database using SQL commands like CREATE DATABASE kong;. Modify kong.conf to include your database connection parameters. For Cassandra, ensure the database cluster is set up and accessible, updating configuration settings accordingly. Adopting best practices like regular backups and security audits is essential to maintain database integrity and performance. Ensuring these steps are meticulously followed lays a robust foundation for utilizing Kong’s full capabilities.
Securing the Kong API Gateway
Efficiently securing the Kong API Gateway is vital to protect APIs from potential vulnerabilities. APIs are often targets for attacks that can exploit weaknesses, resulting in data breaches or denial of service. To mitigate these risks, it’s crucial to understand the security vulnerabilities in APIs, such as insufficient authentication and data exposure.
Authentication methods such as JWT (JSON Web Tokens) and OAuth are commonly implemented to verify the identity of a client requesting access to APIs. These protocols ensure secure communication by validating tokens representing user credentials. JWT is particularly useful for its simplicity and compactness, whereas OAuth provides robust authorization flows suitable for larger applications.
Configuring authorization rules and access control policies further strengthens API security. By defining who can access what resources and actions, you can prevent unauthorized interactions with your services. Leveraging role-based access control (RBAC) mechanisms ensures that permissions are granted based on user roles, minimizing exposure to sensitive data.
For the best outcomes, combine these methods within the Kong API Gateway, ensuring a multi-layered defense strategy. This approach not only shields APIs from attacks but also fosters trust with users by prioritizing the integrity and confidentiality of their interactions.
Traffic Management and Policies
API traffic management in the Kong API Gateway is essential for ensuring smooth operations and optimal performance in a microservices ecosystem. Kong provides robust tools to manage spikes in traffic, which can otherwise overwhelm services. One critical feature is rate limiting, which controls the number of requests a client can make in a specified time frame, safeguarding against potential denial-of-service scenarios.
Additionally, Kong allows for request and response filtering, transforming data flows through the system. This capability enhances flexibility in handling different types of API calls and responses, ensuring consistency and efficiency across your architecture.
Error handling is another significant component of Kong’s traffic management capabilities. By configuring custom error responses, you can deliver informative feedback to clients while preserving the service integrity during unexpected issues. Effective logging strategies complement error handling by recording detailed data about each interaction. This provides invaluable insights into usage patterns and helps in diagnosing and resolving issues quickly.
Overall, with its comprehensive array of features for managing API traffic, Kong serves as a powerful tool to enhance service performance and reliability, tailoring the flow of data for uninterrupted user experiences.
Monitoring and Analytics
To ensure optimal API performance, monitoring Kong involves using various analytics tools and tracking performance metrics. This empowers organizations to identify bottlenecks, understand usage patterns, and respond to issues proactively.
Kong offers integrations with third-party monitoring tools such as Prometheus and Grafana. These tools enable you to visualize metrics, helping you keep an eye on critical aspects such as request rates, latency, and error rates. Setting up dashboards for real-time monitoring provides insights into how effectively the Kong API Gateway is operating within your ecosystem.
Key performance metrics to track include the number of requests processed, response times, and success/error rates. By continuously assessing these metrics, you can ensure your API system operates efficiently, minimizing downtime.
Additionally, analytics play a crucial role in ongoing security assessments. By analysing trends and abnormal patterns, potential vulnerabilities can be spotted early, allowing you to fortify your defences against emerging threats. Implementing comprehensive monitoring solutions not only streamlines API management but also fortifies your microservices architecture, ensuring it remains robust and resilient.
Troubleshooting Common Issues
Kong troubleshooting is crucial for maintaining smooth operations within your API management system. Common challenges often include database connectivity problems, incorrect configuration parameters, and plugin errors. Identifying these issues early is essential to avoid downtime.
Identification of Issues
- Database Connectivity: Verify that your database server is operational and that network configurations allow connectivity. For PostgreSQL, ensure credentials in the
kong.conffile are accurate. - Configuration Errors: Misconfigured settings in the
kong.confcan lead to errors. Double-check for typographical errors or unsupported parameters. - Plugin Issues: Ensure all Kong plugins are compatible with your current version. Update plugins if necessary to resolve compatibility issues.
Effective Troubleshooting Strategies
- Logs and Debugging: Utilize Kong’s comprehensive logging to pinpoint failures. Enable debug mode by adjusting the
log_levelin the configuration file. - Network Testing: Use tools like
pingortelnetto confirm network paths are open. - Version Compatibility: Regularly update to the latest Kong version, ensuring compatibility with all dependencies.
For ongoing difficulties, community forums and official Kong documentation provide invaluable resources for further assistance. These resources are essential for resolving intricate problems efficiently.
Real-World Use Cases
Exploring Kong API use cases offers insights into its effectiveness in enhancing microservices security implementation. Companies across diverse industries have successfully utilized Kong for streamlined API management, paving the way for secure and resilient digital platforms.
Notably, a Fortune 500 retailer revamped its digital strategy by integrating Kong, enhancing security while handling complex transaction loads. This implementation showcased Kong’s ability to effectively manage service connections while leveraging robust security features like rate limiting and OAuth integration.
Another success story highlights a global financial institution employing Kong to automate API governance. The institution significantly reduced manual oversight and minimized risk, demonstrating Kong’s capacity to bolster security frameworks without compromising performance. Its dynamic scalability also played a crucial role in adapting to varying traffic demands, proving indispensable in environments with fluctuating workloads.
Through these success stories, key lessons emerge: organizations emphasize adapting Kong’s tools to meet their unique requirements, ensuring optimal alignment with existing infrastructures. Industries ranging from retail to finance underscore best practices such as regular updates and continuous monitoring, ensuring a fortified and seamless microservices experience. Such real-world use cases underscore Kong’s pivotal role in modern API ecosystems.